In this blog post I am going to describe how you can add co administrators to Azure Stack. In an service provider or enterprise scenario you probably have more than one administrator who manage the environment. Some might be storage admins, some managing the network and others are compute admins. In this post we will only look at the Co Admin on the complete environment. This because I can’t really explain at this time how Azure Stack locations (regions as we know in Azure) and their depended resource providers and related permissions will look like. I hope to discuss this very soon in a future post.
Let’s first look at how RBAC is managed in general in Azure / Azure Stack. If we look at Azure we have these top to bottom resource assignment with the appropriate permission levels. We have at the top an subscription, and in that subscription we have 1 or more resource groups and in resource groups we have the resources. We have some role definitions that contain a permission set we then can assign at each level, like Owner, Contributor and Reader. Custom role definition is something that is released last year in Azure and my assumption that it will come to Azure Stack as well so we can create our own role definitions.
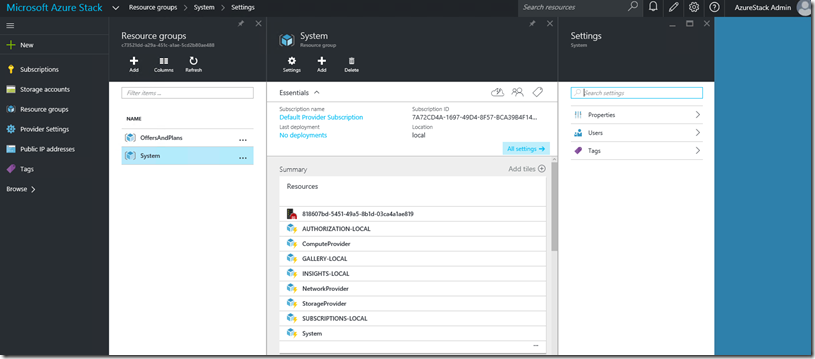
Now if we map this to the Azure Stack Admin side when first log in as Administrator and go to the Subscriptions section we see the Default Provider Subscription. This is the root subscription of the environment:
When we browse to the “Resource Groups” blade we have 2 resource groups. System and OffersandPlans. You see the System resource group is there out of the box and the OffersAndPlans I created when I created a new plan and offer for my tenants. You can match the subscription id in the resource group to the Default Provider Subscription:
So in the System Resource Group the resources are living:
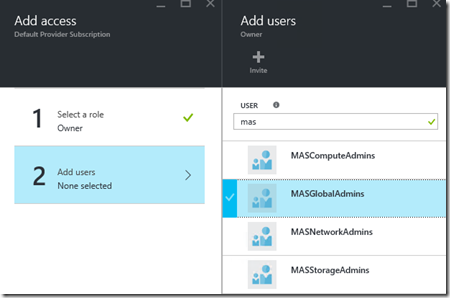
We are able to assign permissions at each level, Subscription, Resource Group or Resource like we can do this in Azure. To add a Co-Admin that has GOD mode on the environment the highest level is the subscription. So we need to add the new user or group to owner list of the subscription. As in this release we have only the option to manage access using Azure AD I have created some groups for delegated access:
Enter the Azure Stack portal with as Administrator. Go to browse in the left navigation pane and choose subscriptions:
Then from left to right follow the red arrows to get to the Add icon:
Select the owner and choose add users. Then type in the group or user name. and choose select and then OK:
NOTE: In my test; Group assignment is not working (yet). When I assign a user it is working flawless.
So now you have GOD mode for other users on your Azure Stack environment.
Mark Scholman
@markscholman